A more secure way of authenticating against those AAD app registrations you say? Yes I do! You don’t need to store those secrets in text environment variables to reference… In this blog post, I’m going to show you how you can securely store your app registration secrets in Azure Key Vault and retrieve them in Power Automate flows for authenticating against registrations for use with HTTP requests / API calls!
Prerequisites
To take advantage of Azure Key Vault, to store your secrets in this way, you’ll need an Azure subscription to register a resource provider in and create an Azure Key Vault.
You’ll also need access to a Power Platform environment with Dataverse provisioned.
Some introduction…
To give a little background here, we can store secret values in multiple ways. We could just stick them into an environment variable as text, but there’s a more secure way. We can store these in Azure Key Vault. When it comes to referencing these secret values, we can use them in Power Automate flows and custom connectors.
We do still have to use environment variables here however we’re no longer storing our secret directly in our variable. Instead we’re storing them in Azure Key Vault and we create an environment variable of ‘secret’ type which references the key vault location. Then we can use actions in our Power Automate flow to securely retrieve the secret value referencing the Key Vault location using our environment variable.
There is some configuration and work we have to do before we can just start creating things though… we have to give Dataverse the permissions it needs to be able to access our secret in Azure Key Vault… a reference to it’s location is simply not enough…
Anyway… time to figure out some secret fun!
Getting prepared for using an Azure Key Vault with Power Platform
So the first thing we need to do is allow the communication between Power Platform / Dataverse and Azure. You’re going to want to go to portal.azure.com and go to an existing or new subscription.
From your subscription you’ll need to go to resource providers under ‘Settings’ in the left hand navigation pane. Then use the search to filter down to Microsoft.PowerPlatform, then you’ll want to select the resource provider titled “Microsoft.PowerPlatform”, select it and then click ‘Register’.
That was easy! Now we can move on to creating our Azure Key Vault.
Creating the Azure Key Vault
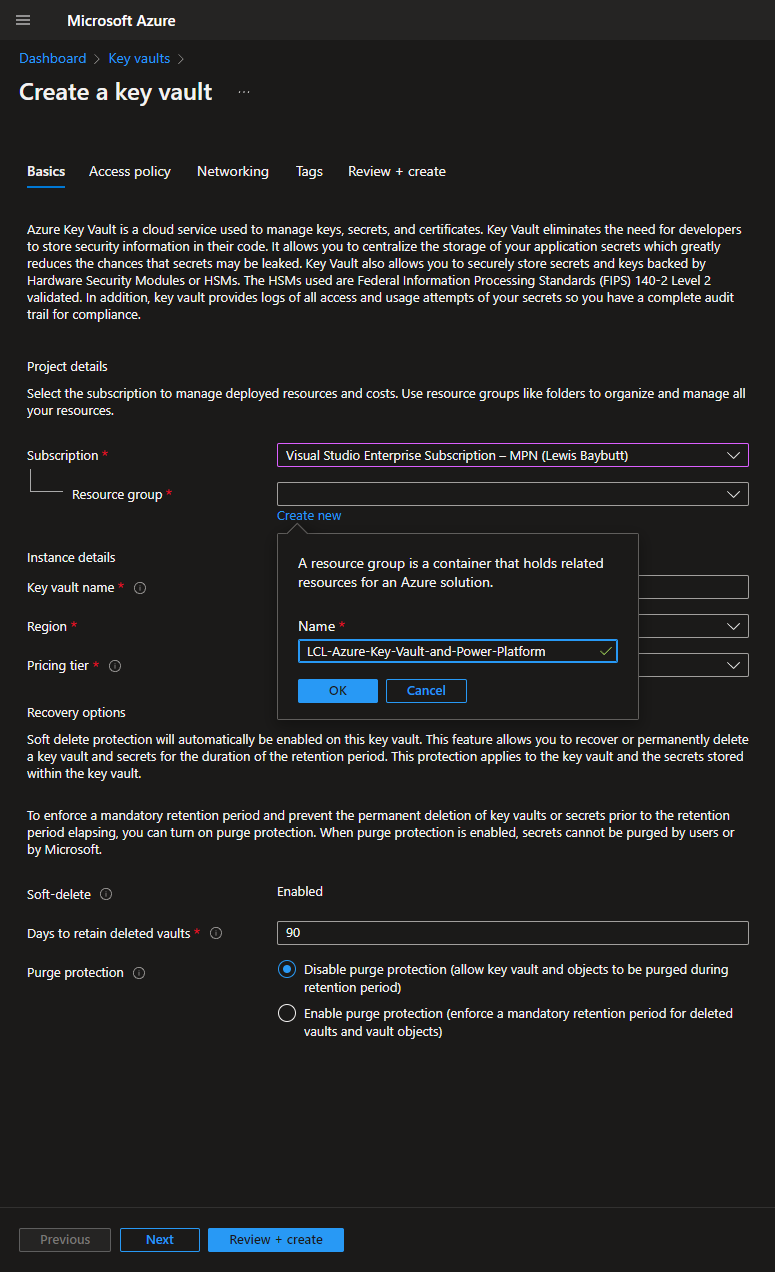
Okay… so now let’s use the search in the Azure portal to find ‘Key Vaults. Once you get there, click ‘create’, to start creating your Azure Key Vault. First you need to select the subscription you want to use to fund your Key Vault ;)… then you need to place it within a resource group. If you haven’t created any resource groups yet, don’t worry you can create one here.
Give your key vault a name, and select the region you want it stored in as well as the pricing tier. In this case I’m sticking with ‘standard’.
We’ll leave everything else as it is for now and select ‘Review + create’
Then click ‘create’ to confirm
You should now see your key vault being deployed to your subscription and resource group. Then you can select ‘Go to resource’ to get to your key vault.
Access control
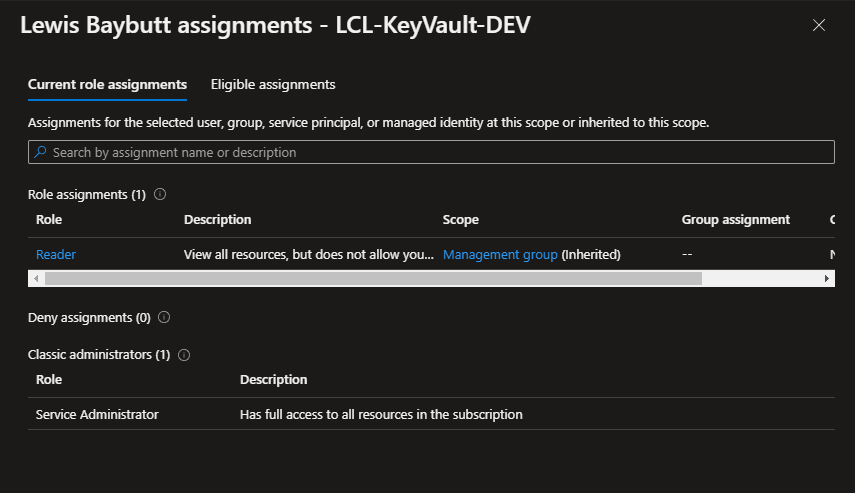
Now we need to make sure that we’re going to be able to access this specific Key Vault. You’ll need to add a role assignment to the user who will create / own the environment variable in your Dataverse environment.
Obviously given we’re just doing some dev fun here, it’ll be me, so I just need to make sure I’ve got access in this instance.
As you can see below, because I’m the creator/owner/Service administrator of the subscription, I have full access to all the resources within the subscription, giving me my needed access to this Key Vault.
GET secret access policy for the Dataverse service principal
So… now we need to make sure that Azure Key Vault has Get secret access policy set for the Dataverse service principal. You’ll want to head to ‘Access Policies’ in your key vault.
Then select ‘create’ so we can create an access policy. Now you’ll want to select the checkbox for ‘Get’ under ‘Secret permissions’. Select next and in the search bar for the principal, search for Dataverse. Select the service principal named ‘Dataverse’ with the identity 00000007-0000-0000-c000-000000000000. Then select next, and again, then ‘review and create’.
WOAH! BREATHEEEE…
Okay… so we’ve done a fair bit of the work now! Now we can start to add secrets into our Key Vault for use in our Power Automate flows!
Creating a secret
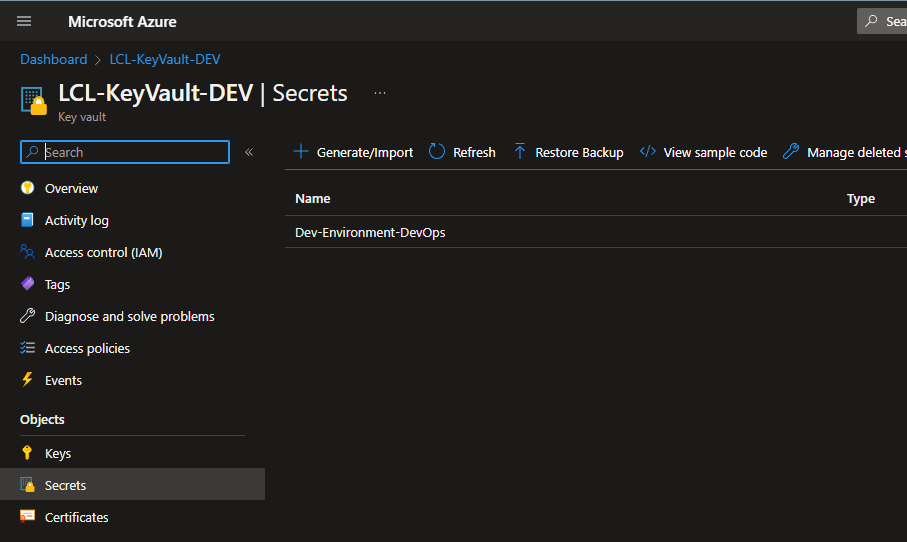
Head to ‘secrets’ in your Key vault and select ‘Generate/import’. Leave the upload option as manual and give your secret a unique name. Then paste in your secret value for the secret you want to store (string). Leave the other options as they are and select create.
Awesome! I’ve now got the secret for an app registration I wanted to store somewhere, stored in Azure Key Vault!
The Power Platform Part…
So, we’ve mainly focused on the Azure side until now. Let’s recap. We registered a resource provider in our subscription for Power Platform, we created an Azure Key Vault and deployed it in a resource group within our subscription, we applied appropriate access control to our Key Vault, we applied the GET secret access policy for the Dataverse service principal in our Key Vault, and we finally created a secret in our Key Vault!
Now… the next part is to of course be able to use and reference that secret!
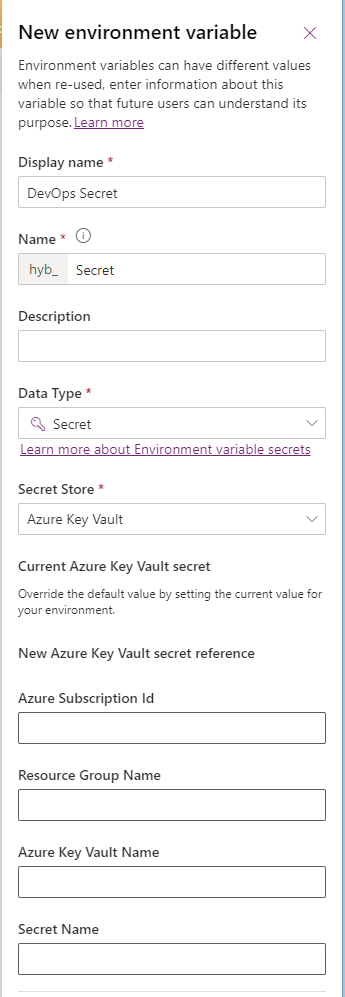
Creating the environment variable
So I’ve got an unmanaged solution at make.powerautomate.com where I’m going to create an environment variable. I’m going to need a few things to paste in here first…
I’ll need the subscription ID that my resource group and key vault is held in. I’ll need my resource group name that my key vault is located in. I’ll need my key vault name that my secret is located in and finally I’ll need my secret name.
From here, go ahead and create a new environment variable in your unmanaged solution. Give it a name and choose ‘Secret’ as the data type. Then select ‘Azure Key Vault’ as the Secret Store. Then select ‘New Azure Key Vault secret reference’. Here paste in the values we collected a moment ago.
Then select save to create your environment variable.
Now, we have our environment variable referencing our secret stored in Azure Key Vault. It’s important to remember that this isn’t an environment variable storing our secret and rather references a location with our secret in. Due to this, and the current functionality here, we can’t simply reference this environment variable as dynamic content to output our secret in a flow. We have one more step…
Retrieving our secret for use in a flow
Now let’s create a flow to test this out. Simply click new in your solution, automation, cloud flow and select instant to create an instant button cloud flow.
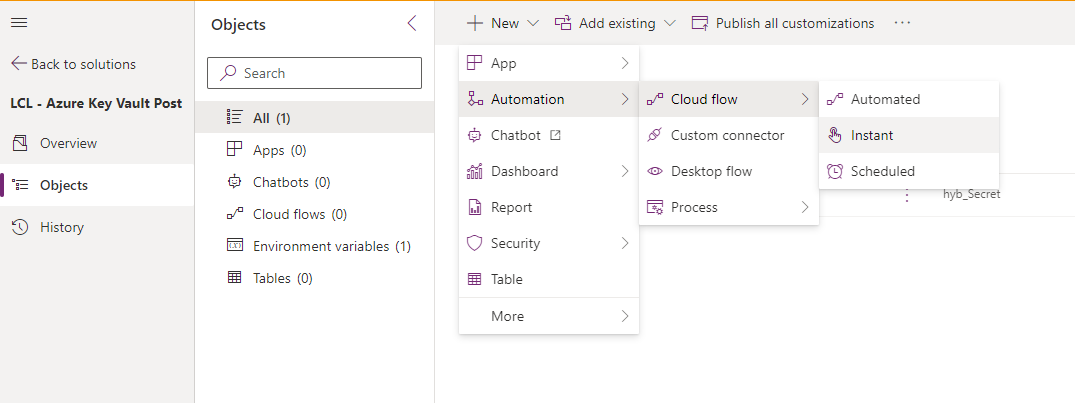
You’ll want to add a step to your flow called ‘Perform an unbound action’ which is against the Microsoft Dataverse connector.
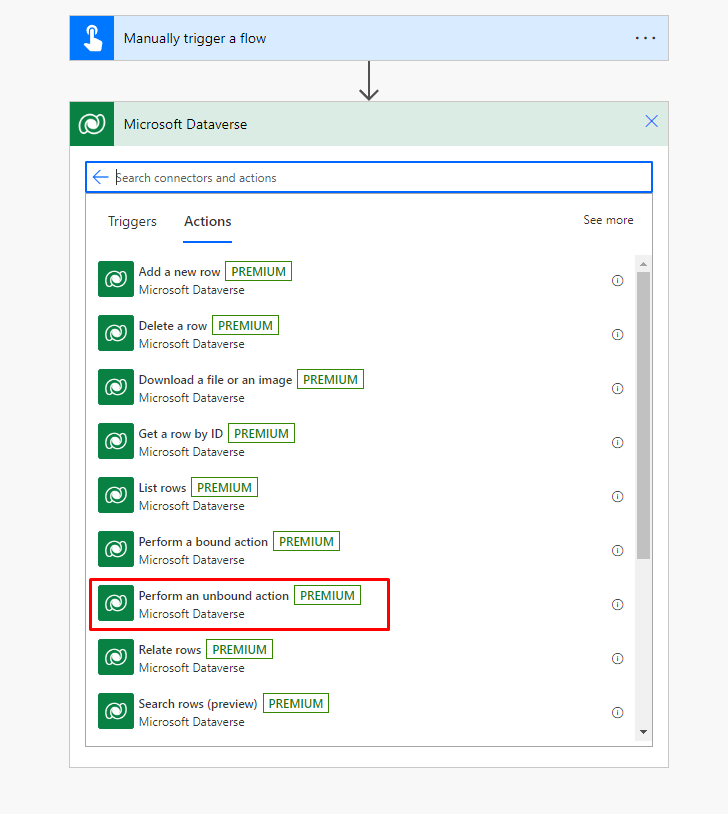
Now we need to select our action from the options the flow step gives us. We need to select the action: RetrieveEnvironmentVariableSecretValue
Then we need to populate our environment variable name. We’re still not using any dynamic content here. Do not expect that your secret environment variable will show up at all as dynamic content. Here we want to paste in the name (not the display name) of our environment variable exactly.
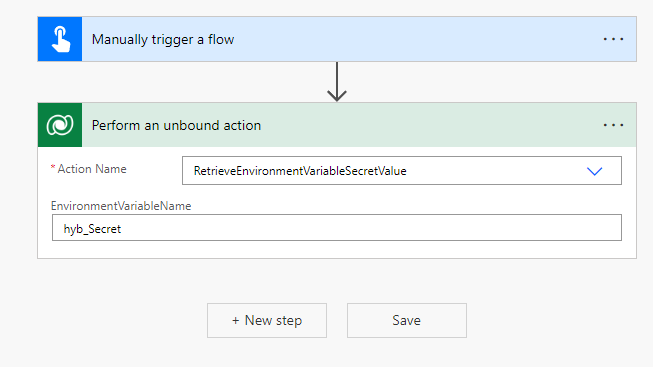
Now we will be able to get back our secret for use in our flow as dynamic content from the outputs of this step! But WAIT!!!
This has created a little loophole in our security attempts here. Imagine if someone went over my flow runs, they could now find my secret and use it as they please… I don’t want this so I’m going to head to the settings of this flow step, and switch on Secure Outputs which will prevent my outputs being displayed in any flow runs in the history.
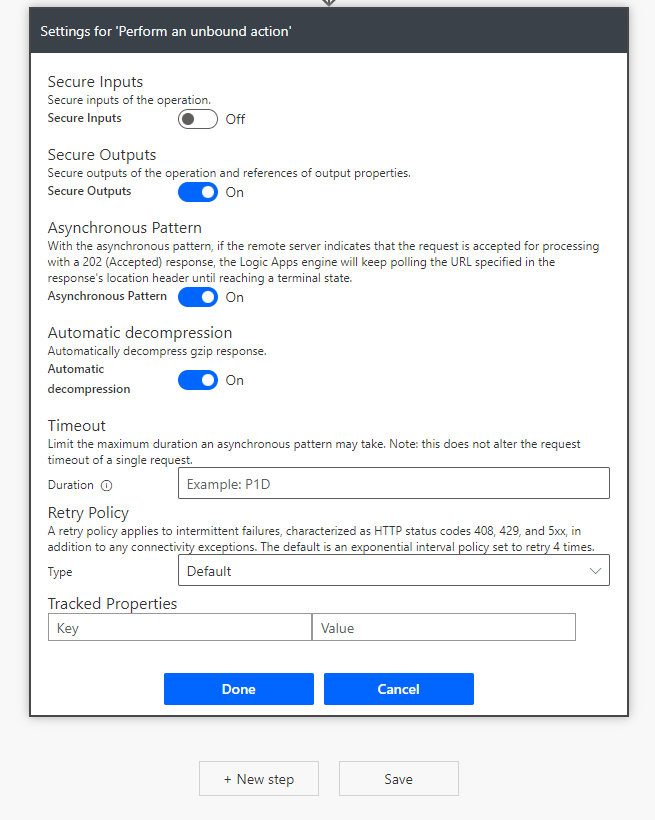
You can now use the secure dynamic content in this step as inputs to a HTTP request! Make sure you switch on Secure Inputs in that HTTP request step so that your secret isn’t exposed in flow run history as an input on that step.
That’s it!
So, that’s how you use Azure Key Vault to secure your secrets away for referencing via environment variables in flows! I hope this post helped. If you have any comments or questions, drop them down below in the comments 🙂

